Overview
Previously we have covered a process on how to change SSH port on your remote server(POST). Next in this article, we will show you how to setup a passwordless SSH connection on Linux. To setup a passwordless SSH connection is very secure and a good practice for hardening your server. It is more secure than any other strong password, really difficult to hack and effortless to set up.
This guide will help you to set up a passwordless SSH authentication on Linux with a help of SSH keypair that are located on any Linux or Unix-base operating systems.
We’ll be demonstrating examples how to setup a passwordless SSH connection on a local Linux machine in a LAN network and on a Cloud Linux machine too.
How to setup a passwordless SSH connection on Linux
Step 1: Generate SSH keys on your local system
First, you need to generate an SSH private and public key on your local Linux machine. Run the following command to generate an RSA key pair using the ssh-keygen command:
ssh-keygen -t rsa
- You can define the path to save the key files.
- Press the Enter key to Save the key to default location.
- Now, It will ask you to set a passphrase for your keys.
- Enter passphrase (empty for no passphrase).
- Again, leave it blank by pressing the Enter key. On successful key files generation, you should see the following output.
Output:
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa
Your public key has been saved in /root/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:4oR5vsglUcjom3oEqewbUrKNHhc5imiGK1h0GVSotXc [email protected]
The key's randomart image is:
+---[RSA 3072]----+
| ..o. |
| o+. |
| ..oo+. |
|o.o =+. E |
|+oo=+.+.S |
|=B+oo* . |
|XO+.. + |
|B+=. + . |
|++. o . |
+----[SHA256]-----+
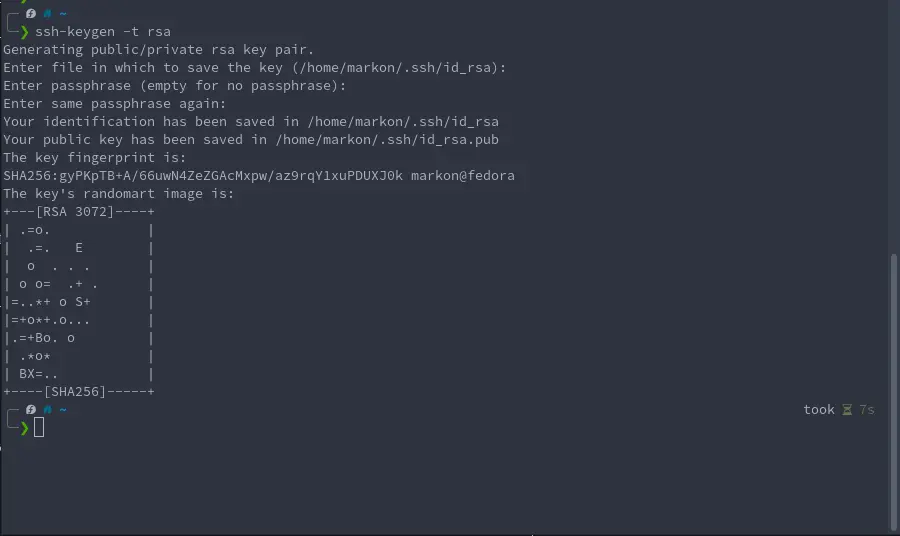
Next, verify the public and private key using the following command:
ls -l .ssh/id_rsa*
Output:
-rw------- 1 root root 2602 Aug 3 15:48 .ssh/id_rsa
-rw-r--r-- 1 root root 570 Aug 3 15:48 .ssh/id_rsa.pub
NOTE: For the demonstration purposes, we generated and used the RSA key encryption on our ssh key. It is now recommended that you do not use RSA encryption on the keys anymore since the RSA encryption is becoming old and it may become breakable in the future and switch and use other encryption types on the keys such as ECDSA or ED25519. This is even suggested on the official SSH docs page as well.
If you still wish to use the RSA key type, then at least it’s suggested to use at 4096 bits key size.
Step 2: Upload SSH public Key to the Remote Server
Now, you need to upload your local machine public key to the remote server. Using ssh-copy-id command, you can copy the public key to the remote server:
syntax:
ssh-copy-id root@remote-server-ip
Example:
ssh-copy-id [email protected]
Enter your remote server password to copy the public key to the remote server.
Output:
/usr/bin/ssh-copy-id: INFO: Source of key(s) to be installed: "/root/.ssh/id_rsa.pub"
The authenticity of host '161.35.92.86 (161.35.92.86)' can't be established.
ED25519 key fingerprint is SHA256:3TDbnjPHbdGyL1ovbSMwotvM2h5IHXQxs4j+gt9yY38.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
/usr/bin/ssh-copy-id: INFO: attempting to log in with the new key(s), to filter out any that are already installed
/usr/bin/ssh-copy-id: INFO: 1 key(s) remain to be installed -- if you are prompted now it is to install the new keys
[email protected]'s password:
Number of key(s) added: 1
Now try logging into the machine, with: "ssh '[email protected]'"
and check to make sure that only the key(s) you wanted were added.
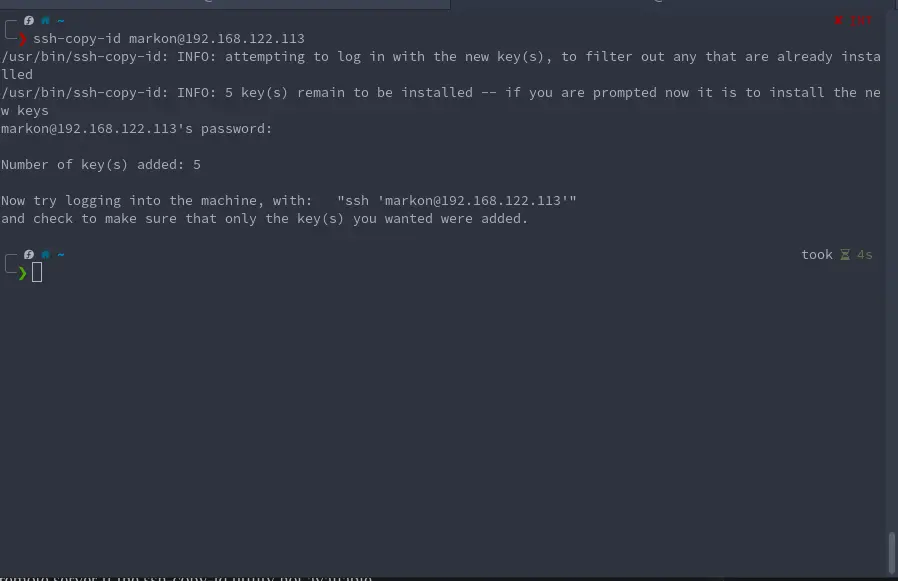
Running this command will not just copy over the keys you just create but it will also copy over all the keys you have on your local machine that are located in the “./ssh” folder.
Alternatively, you can execute the following command to copy public key to the remote server if the ssh-copy-id utility not available on your local system.
cat ~/.ssh/id_rsa.pub | ssh [email protected] "mkdir -p ~/.ssh && chmod 700 ~/.ssh && cat >> ~/.ssh/authorized_keys && chmod 600 ~/.ssh/authorized_keys"
In the above command, replace your username and remote server IP address. Also note that .ssh folder permission should be 700 and authorized_keys permission should be 600
The following output shows you the folder and file permission:
drwx------ 2 root root 4096 Aug 3 10:56 .ssh/
-rw------- 1 root root 0 Aug 3 10:56 authorized_keys
If you have different directory and file permission then you can set permission manually by executing the following command:
chmod 700 ~/.ssh
chmod 600 ~/.ssh/authorized_keys
Step 3: Connect to the Remote Server without using password:
Your public key copied on the remote server, and Now you should be able to connect to the remote server without password:
Syntax:
ssh root@your-server-ip
After executing the above command, you should be logged in to your remote server without any password.
Create custom SSH key and other key types
As we mentioned earlier, RSA is not the only key type and we used only RSA for demonstration. In the following part of the post we’ll be demonstrating how to create ECDSA SSH key, how to create ED25519 SSH key and how to create a custom SSH key with a custom name, comment and file location.
Generate EDCSA SSH key
The following command showcases how to generate the ECDSA SSH key. We use option "-b" to choose the key size and for ECDSA 521 bits is the stronger key size.
ssh-keygen -t ecdsa -b 521
Generate ED25519 SSH key
The following command showcases how to generate the ED25519 SSH key. At the moment ED25519 has only one key size.
ssh-keygen -t ed25519
Generate a custom SSH key with a custom filename
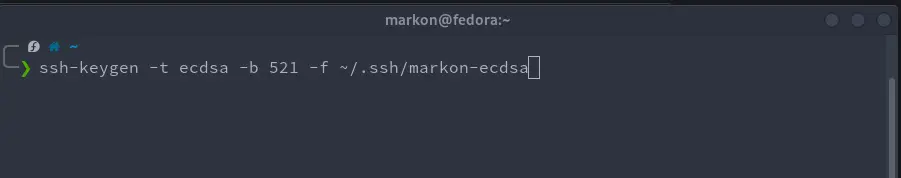
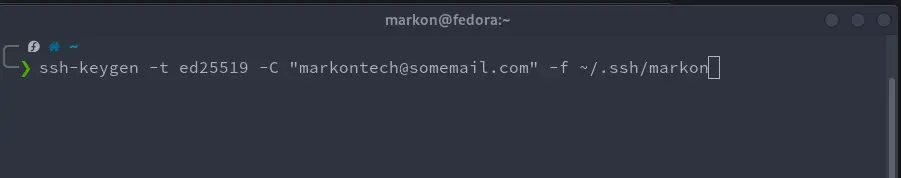
The following commands are examples how to generate SSH key with a custom filename and comment. We used option "-C" to define the comment that will be written at the end of key files. Option "-f" is used to define the filename of key files and where are they going to be saved on your computer.
ssh-keygen -t ed25519 -C "[email protected]" -f ~/.ssh/markontech
ssh-keygen -t ecdsa -b 521 -f ~/.ssh/markon-ecdsa
Wrapping up
To summarize the steps we executed in this article on how to setup a passwordless SSH connection on Linux.
We have generated SSH key-pair on the client system and set up the public key to the remote server and accessed the remote server without using a password. Passwordless SSH connection is also helpful in cronjob where you want to perform administrator’s task like backup the system, copy files from remote server, automate updates and many other tasks. You are welcome to ask me if you have any query related to passwordless SSH.
Thank you for your time…